- Aug 20, 2022
- 4,956
- 12,677
- 113
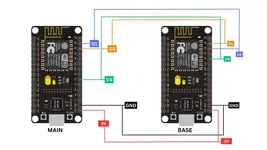
V2 UPDATE
MaskFi – WiFi Security Awareness & Testing Tool
- MaskFi is an advanced penetration testing tool designed to simulate WiFi security vulnerabilities by leveraging techniques such as deauthentication attacks, rogue access points, and captive portals. By creating deceptive networks, it allows cybersecurity professionals and ethical häçkers to assess how attackers can exploit unsecured WiFi networks and s†éál sensitive information.
Deauthentication Attack – Disconnects users from legitimate networks to force reconnections.
Rogue AP Simulation – Creates a fake WiFi hotspot to mimic trusted networks.
Captive Portal Phishing – Redirects users to a controlled login page for credential harvesting awareness.
Packet Monitoring & Analysis – Helps identify security flaws in network traffic.
This project is strictly for educational and security awareness purposes. MaskFi is intended to help users understand the importance of WiFi security and how attackers exploit weak networks. Unauthorized use of this tool on networks you do not own or have explicit permission to test is îllégâl and unethical. The responsibility lies with the user to comply with ethical häçking laws and responsible disclosure policies.
Stay safe. Stay ethical. Learn to secure.
How to Use MaskFi
MaskFi is a WiFi security testing tool designed to demonstrate vulnerabilities in wireless networks using techniques like deauthentication attacks, rogue access points, and captive portals. Follow these steps to configure and run MaskFi effectively.
1. Open MaskFi
Run the tool on a compatible system and navigate to the Settings menu to configure the attack parameters.
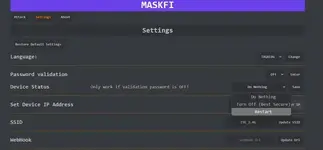
2. Configure Settings
Language: Select your preferred language.
Password Validation: Toggle password validation to ON to enable login security checks.
Set Device IP Address: Choose a network provider or manually set an IP address.
SSID Selection: Enter the target SSID of the network you want to simulate or attack.
Webhook URL: If using an external logging system, enter a valid webhook URL for capturing data.
3. Start an Attack
Navigate to the Attack tab and select the type of test you want to perform:
Deauthentication Attack: Disconnects users from a network, forcing them to reconnect.
Rogue AP Simulation: Creates a fake WiFi hotspot mimicking the target SSID.
Captive Portal Phishing: Redirects users to a controlled login page to demonstrate credential interception risks.
4. Monitor and Analyze
Once the attack is running, monitor the results through the logs. Ensure all tests are conducted ethically and with permission.
5. Restore Default Settings (Optional)
If you need to reset configurations, click "Restore Default Settings" to revert all changes.
If you want to obtain the target's password just once, disable Password Validation in the settings. You can also try this on your own device by accessing 192.168.1.1.
You must reply before you can see the hidden data contained here.
